🔐🔐Guide to managing security vulnerabilities in your dependencies using Github 🔐🔐
You might have come across a message on your Github repos notifying you of out-of-date dependencies. It looks like this:
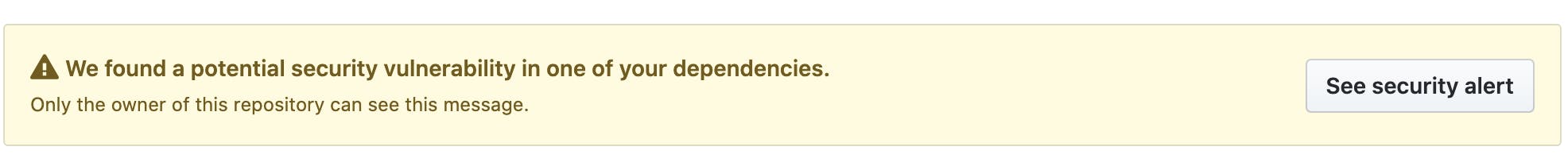
Why am I getting these alerts?
GitHub detects and alerts on vulnerable dependencies in public repositories by default. You'll be alerted anytime a vulnerability is discovered in your project. For private repositories, maintainers will need to enable the dependency graph and security alerts.
A vulnerability is a problem in a project's code that could be exploited to damage the confidentiality, integrity, or availability of the project or other projects that use its code. A vulnerabilities severity level is defined by the Common Vulnerability Scoring System (CVSS). Github assigns one of four possible severity levels; critical, high, moderate, and low. Depending on the severity level and the way your project uses the dependency, vulnerabilities can cause a range of problems for your project or the people who use it.
Github keeps track of known vulnerabilities via an in-house vulnerabilities database known as the Github Advisory Database. The database contains a curated list of security vulnerabilities, from several sources.
How does Github know these vulnerabilities exist in my project?
Github scans dependency management manifests, such as a pipfile, or package.json file in your public repo and matches up the version numbers with what exists within its advisory database to find out which versions are unpatched. When a new vulnerability is added to the database, Github identifies repositories that use the affected version of the dependency, send a security alert to repository maintainers, and generate an automated security update request. Each request includes information on the affected package, as well as the vulnerable and patched versions.
How do I fix things up?
Automatic updates can be configured on the repository to generate Pull requests that update the package versions. Manual updates to package versions also work fine.
Clicking on Create automated security update will generate a PR that updates the dependency versions.
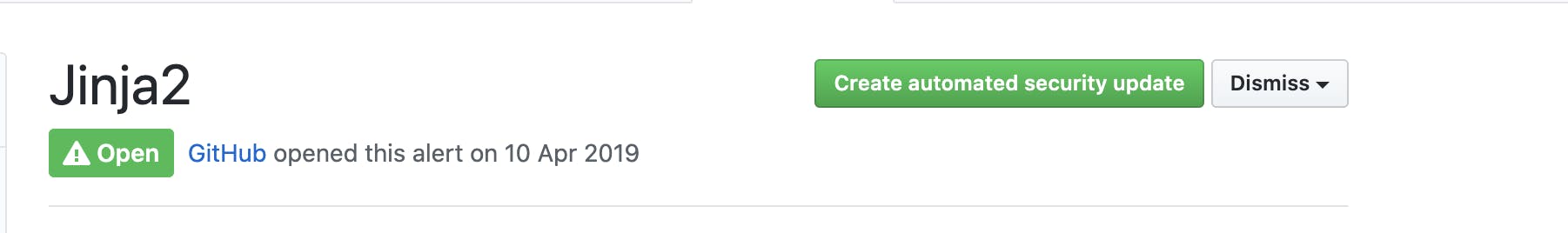
When you merge the pull request, the corresponding security alert is marked as resolved for your repository.
Sometimes, a pull request cannot be automatically created as one or more other dependencies may require a version that is incompatible with the update. In that case, you'll have to manually update the dependency on a new branch and test that all affected versions and additional dependencies work fine. You can then merge in the fix. The alert will then be marked as resolved. 🎉🎉
Credits
- GitHub Documentation on Security Alerts
- Cover Image by Manypixels.co